Main Page>Table of contents>TCP/IP introduction>
The Transmission Control Protocol/Internet Protocol (TCP/IP) suite was created by the Department of Defense (DoD) to ensure and preserve data integrity, as well as maintain communications in the event of catastrophic war. If designed and implemented correctly, a TCP/IP network can be a dependable and resilient one.
TCP/IP and the DoD Model
The DoD model is a condensed version of the OSI model. It is com-prised of four, instead of seven, layers:
Next Figure shows a comparison of the DoD model and the OSI referencemodel. As you can see, the two are similar in concept, but each has a differentnumber of layers with different names.
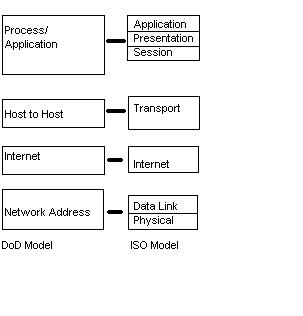
FIGURE 2 .1 The DoD and OSI models
A vast array of protocols combine at the DoD modelís Process/Application layer to integrate the various activities and duties spanning the focus of the OSIís corresponding top three layers (Application, Presentation, and Ses-sion). The Process/Application layer defines protocols for node-to-node application communication and also controls user-interface specifications.
The Host-to-Host layer parallels the functions of the OSIís Transport layer, defining protocols for setting up the level of transmission service for applications. It tackles issues like creating reliable end-to-end communication and ensuring the error-free delivery of data. It handles packet sequencing and maintains data integrity.
The Internet layer corresponds to the OSIís Network layer, designating the protocols relating to the logical transmission of packets over the entire network. It takes care of the addressing of hosts by giving them an IP (Internet Protocol) address, and it handles the routing of packets among multiple networks. It also controls the communication flow between two hosts.
At the bottom of the model, the Network Access layer monitors the data exchange between the host and the network. The equivalent of the Data Link and Physical layers of the OSI model, the Network Access layer oversees hardware addressing and defines protocols for the physical transmission of data.
While the DoD and OSI models are alike in design and concept and have similar functions in similar places, how those functions occur is different.
Figure 2.2 shows the TCP/IP protocol suite and how its protocols relate to the DoD model layers.
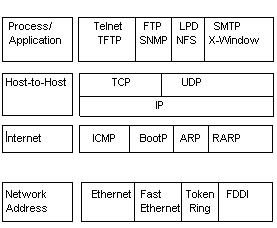
FIGURE 2 .2 The TCP/IP protocol suite